The economy and businesses closely rely on network infrastructures functioning efficiently. Minor network bottlenecks and snags can cost companies a good chunk of money and...
Latest Posts

Mindful cybersecurity: 5 cybersecurity strategies for stress-free living
Keeping a stress-free and thoughtful approach to cybersecurity requires implementing tactics that put security and wellbeing first. The following five cybersecurity techniques will help in...

Happy National IT Service Provider Day: Celebrating the unsung heroes
Have you ever wondered how your favorite online store stays operational 24/7, or how your company seamlessly connects employees across the globe? The secret behind...

The role of DDI solutions in optimizing smart manufacturing network infrastructures
The Fourth Industrial Revolution, or Industry 4.0, has integrated digital technologies such as the Industrial Internet of Things (IIoT), operational technology, and information technology into...

Postgres performance monitoring: Best practices and key metrics
Before diving into how to ensure the reliability, availability, and optimal performance of your PostgreSQL database, it’s essential to understand the necessity of constant vigilance...

Top tips: How to avoid getting your juice jacked
Top tips is a weekly column where we highlight what’s trending in the tech world today and list out ways to explore these trends. Ever...

How to monitor Apache web server performance metrics
Apache, the world’s most popular web server software, powers an estimated 30.2% of all active websites. Known for its reliability, flexibility, and robust features, Apache...

OpUtils’ IP scanner for visibility: See everything, manage effortlessly
Organizational networks, especially the larger ones, expand beyond the physical infrastructures into cloud platforms, making the network more intricate. This makes gaining real-time visibility difficult...
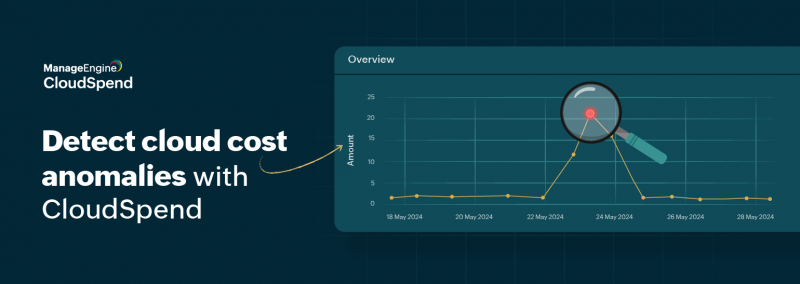
CloudSpend’s Zia framework: Top 5 ways to detect cloud cost anomalies
CloudSpend’s Zia framework, powered by AI, is designed to detect any unexpected spikes or irregularities in your cloud expenses. The Zia Anomaly Report aids in...
