Organizational networks, especially the larger ones, expand beyond the physical infrastructures into cloud platforms, making the network more intricate. This makes gaining real-time visibility difficult...
Latest Posts
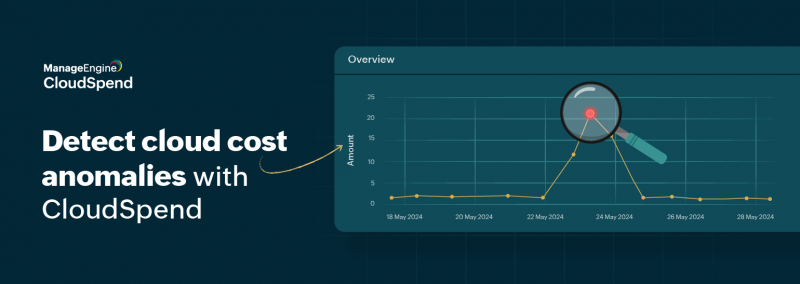
CloudSpend’s Zia framework: Top 5 ways to detect cloud cost anomalies
CloudSpend’s Zia framework, powered by AI, is designed to detect any unexpected spikes or irregularities in your cloud expenses. The Zia Anomaly Report aids in...

Mastering Hyper-V monitoring: Overcome virtualization challenges with OpManager
The before and after of virtualization in network monitoring is stark. Before virtualization, IT admins battled resource constraints, scalability limitations, security and isolation concerns, maintenance...

What is DHCP fingerprinting? How does it work and how to configure it in DDI Central?
Network infrastructures in many industries today are challenged by a surge of connected devices, especially as IoTs and BYODs are increasingly popular. The complexity and...

Top tips: Wearable tech etiquette in the workplace
Top tips is a weekly column where we highlight what’s trending in the tech world today and list ways to explore these trends. This week,...

Revolutionize storage monitoring with our new, comprehensive e-book
According to Forrester Research, 47% of IT companies identify data growth as one of their top three challenges. Regardless of the size of your enterprise...

April 2024 Patch Tuesday comes with fixes for 149 vulnerabilities, no zero-days
This blog has been updated to include the details of the zero-day vulnerabilities that were not marked initially by Microsoft Details of the zero-days CVE-2024-26234...

Identity Management Day: Protecting your digital footprint
Identity Management Day occurs on the second Tuesday of April, April 9 this year. It was established by the Identity Defined Security Alliance in 2021...

The role of DDI solutions in optimizing network performance in banking, financial services, and insurance companies
In the high-stakes world of banking, financial services, and insurance (BFSI), collectively known as the finance sector, where transactions occur in milliseconds and financial destinies...
