Without proper data center remote access management, administrators invite security issues and waste time.
With more organizations adopting cloud computing and virtualization, data center operations have been proliferating across the globe. This trend creates multiple challenges for data center administrators in IT organizations. These admins need to ensure not only performance and resource utilization, but also data security.
Usually, data centers are located in strategic sites due to factors such as physical security, climatic conditions, environmental factors, and availability of telecommunications and networking facilities. Because keeping the IT workforce at the data centers is neither feasible nor desirable, organizations prefer remote access to IT resources.
In a typical mid-sized company, an administrator needs to connect to data center resources about 50 times during a shift. In many cases, the admin needs to respond to business requests instantly. Some of the common tasks admins perform on data center resources include:
Server-related operations — Admins might need to deploy new applications or application libraries in servers, change the factory default settings of applications running in machines, restart an application, change the settings of a server in production, change security configurations, analyze logs, or troubleshoot when a server goes down.
Network device-related tasks — Admins might also need to change firewall settings, analyze the traffic flow in switches, review device configurations, perform firmware upgrades, install patches, make changes to device configurations in response to security alerts from device vendors, change access control lists of devices, and in emergency situations like a network outage, take corrective action to get the network or device up and running.
Admins are also required to perform various other tasks on Power Distribution Units (PDU) too.
Challenges in data center remote access
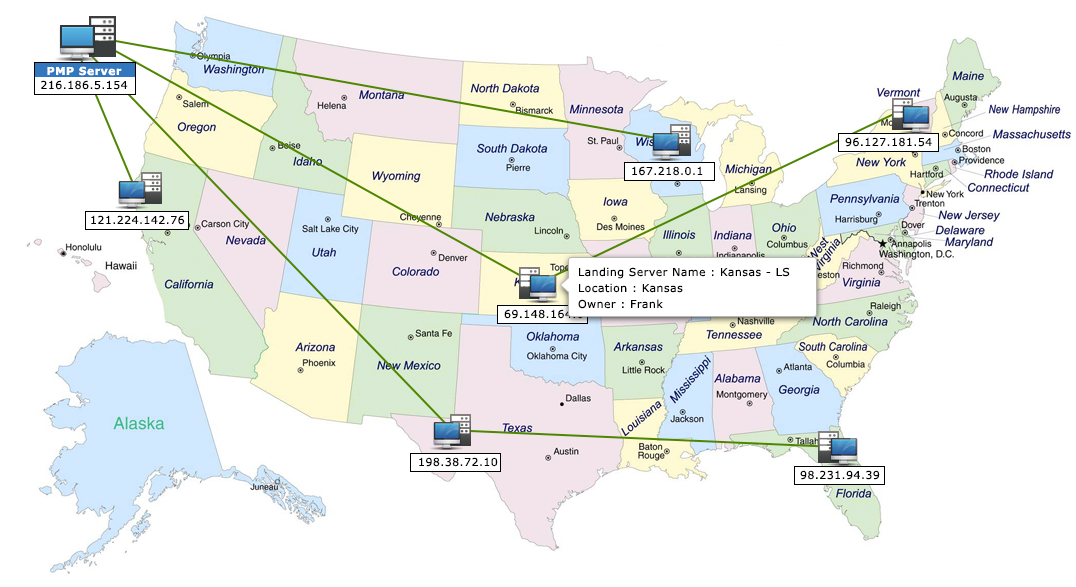
Data centers usually limit direct access to remote devices via SSH and Telnet connections due to security reasons and network segmentation. Consequently, data center administrators working remotely must first connect to an intermediate landing server (also known as jump server) and then “hop” to the target system.
In some cases, an admin must make multiple hops before ultimately connecting to the target device. At each step of the remote access process – from the initial landing server to each subsequent hop and the target device – the admin must provide the user name and password as well as know the IP address of the landing server.
When a problem strikes, administrators often struggle to trace the credentials and connectivity details — including IP addresses, user names, and passwords — for data center resources and jump servers. That cumbersome and time-consuming process for remotely accessing the data center means that administrators are frequently unable to respond to business priorities in a timely manner.
Controlling and monitoring remote access
Not only are the traditional remote access practices cumbersome, they also lack access controls.
Administrative passwords, which grant unlimited access privileges on the IT assets in data centers – are mostly stored in plain text in volatile sources such as sticky notes, spreadsheets, printouts, and text documents, and insecurely shared among technicians, leaving the data center open to security attacks. Anyone with access to the spreadsheet could get unlimited privileged access to the data center resources.
Even when authorized users get access, it is extremely important to monitor privileged access on sensitive resources. A disgruntled insider could easily plant a logic bomb or steal customer data. Traditional practices lack monitoring provisions.
Robust, one-click, controlled access to data center remote access: Need of the hour
Consider a scenario where one can access critical data center resources with a mouse click without bypassing security restrictions. Password Manager Pro, the privileged password management solution from ManageEngine, makes data center remote access a breeze.
Instead of requiring users to authenticate themselves at every hop and at the remote device, Password Manager Pro handles all login and authentication steps automatically, giving admins one-click access to their remote data center resources. This way, data center remote access becomes several times faster, helping you achieve increased operational efficiency and productivity.
Password Manager Pro centralizes the management of all those credentials and access controls, so users are spared the burden of authenticating themselves at each stage of remote access.
Administrators can configure landing servers and their login credentials and then associate the servers with the resources being managed by Password Manager Pro. In turn, admins can launch a one-click connection with remote resources without worrying about the intermediate hops. While the admin experiences a direct connection, Password Manager Pro automatically executes all of the intermediate hops in the background, establishing a connection with each landing server and finally with the remote resource.
In addition to gaining remote access, administrators can also use the landing server configuration in Password Manager Pro to reset passwords of data center equipment that are multiple hops away. Admins can change passwords as well as verify that passwords stored in Password Manager Pro are the same as the passwords associated with the resources and with the remote access.
With Password Manager Pro, there is no direct connectivity between the admin’s device and remote host. The connection is always tunneled through the Password Manager Pro server. Similarly, passwords needed to establish remote sessions do not need to be available at the user’s browser. These mechanisms combine to establish highly secure, extremely simple remote access.
Beyond remote access
Password Manager Pro also facilitates video recording of the privileged sessions launched from Password Manager Pro. The recordings can be archived and played back to support forensic audits and let enterprises monitor all actions performed by privileged accounts during privileged sessions.
Session recording caters to the audit and compliance requirements of organizations that mandate proactive monitoring of activities. Administrators can readily answer questions regarding the “who, what, and when” of privileged access. In addition, administrators may terminate sessions in real time if any suspicious activity is found, giving admins complete control over privileged sessions.
Remote access management, the first step in DCIM
Data center infrastructure management is gaining ground and the market is flooded with various types of DCIM solutions. However, remote access management (RAM) often remains a neglected area. Though data center managers are aware of the ever-increasing cyber-attacks, they fail to recognize the importance of a robust remote access control solution until they encounter a security issue. In fact, RAM is the first step in DCIM. Fast, reliable, and secure one-click access to data center resources coupled with controlling and monitoring provisions is crucial for data center security.
Bala
Password Manager Pro – Quick Video | Free Trial Download | White Papers | Success Stories